Find My Pass
I managed to forget my password for my KeePass Database but luckily I had it still open and managed to get a dump of the system's memory. Can you please help me recover my password?
- Download https://mega.nz/#!IdUVwY6I!uJWGZ932xab44H4EJ-zVAqu6_UWNJcCVA4_PPXdqCyc
- Download #2 https://drive.google.com/open?id=1hUlGqJZYgbWaEu7w0JnPMqgYdFr8qVJe
- Download password:
eD99mLkU
Hint! I am not very good with computers, I use my one safe password where I want to keep everything safe from hackers.
Recon
Both URLs link to HackTM.zip, which is 365MB. The unpacked file HackTM.vmem is 2GB, which seems to be a VM memory file.
volatility
An interesting string from the vmem file: \\HACKTM-PC\Users.HackTM\Desktop\Pass.kdbx
The KeePass XML file can be found in the VMEM file split in four parts in the following memory locations:
58C37768583B800057FB90005863A000
Combine and fetch from those location to create the full Keepass XML file: link
2 7zip files can be found in that XML file, but they do not contain the flag.
volatility info
Going forward, we used information from an unrelated CTF write-up that
covers keepass+volatility. We also found this gist
helpful in understanding the .kdbx file format.
$ volatility -f HackTM.vmem imageinfo
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x86_23418, Win7SP0x86, Win7SP1x86_24000, Win7SP1x86
AS Layer1 : IA32PagedMemoryPae (Kernel AS)
AS Layer2 : FileAddressSpace (/root/hacktm/HackTM.vmem)
PAE type : PAE
DTB : 0x185000L
KDBG : 0x82b7cb78L
Number of Processors : 2
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0x80b96000L
KPCR for CPU 1 : 0x807ca000L
KUSER_SHARED_DATA : 0xffdf0000L
Image date and time : 2019-11-11 20:50:09 UTC+0000
Image local date and time : 2019-11-11 12:50:09 -0800
volatility plist
$ volatility -f HackTM.vmem --profile=Win7SP1x86 pslist
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit
---------- -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------
0x84a41800 System 4 0 97 410 ------ 0 2019-11-11 20:49:19 UTC+0000
0x8625aa30 smss.exe 280 4 5 30 ------ 0 2019-11-11 20:49:19 UTC+0000
0x863c5d20 csrss.exe 380 360 9 632 0 0 2019-11-11 20:49:22 UTC+0000
0x85fff1e0 wininit.exe 432 360 7 92 0 0 2019-11-11 20:49:22 UTC+0000
0x85fffd20 csrss.exe 440 424 10 220 1 0 2019-11-11 20:49:22 UTC+0000
0x86438c00 services.exe 484 432 25 270 0 0 2019-11-11 20:49:22 UTC+0000
[...]
0x86e1b810 KeePass.exe 3620 1988 10 251 1 0 2019-11-11 20:49:46 UTC+0000
Keepass
Found a running Keepass instance. We dump the process:
$ volatility -f HackTM.vmem --profile=Win7SP1x86 memdump -p 3620 -D dump
Writing KeePass.exe [ 3620] to 3620.dmp
And the clipboard while we're at it:
$ volatility -f HackTM.vmem --profile=Win7SP1x86 clipboard
Session WindowStation Format Handle Object Data
---------- ------------- ------------------ ---------- ---------- --------------------------------------------------
1 WinSta0 0xc009L 0x7017b 0xfe9a05a8
1 WinSta0 CF_TEXT 0xd ----------
1 WinSta0 0x2000L 0x0 ----------
1 WinSta0 CF_TEXT 0x2000 ----------
1 WinSta0 0xd0095L 0x0 ----------
1 WinSta0 CF_TEXT 0x1 ----------
1 ------------- ------------------ 0xe00cb 0xffbb46b0
1 ------------- ------------------ 0xd0095 0xfddf5300
1 ------------- ------------------ 0xb0137 0xfd4b47b0
Side-note; to view the contents of the clipboard, we must use the -v because volatility ¯\_(ツ)_/¯.
0xffbb46bc 64 00 6d 00 56 00 5a 00 51 00 6d 00 64 00 7a 00 d.m.V.Z.Q.m.d.z.
0xffbb46cc 4f 00 6c 00 55 00 72 00 63 00 45 00 42 00 6c 00 O.l.U.r.c.E.B.l.
0xffbb46dc 52 00 6a 00 38 00 37 00 64 00 48 00 51 00 33 00 R.j.8.7.d.H.Q.3.
0xffbb46ec 55 00 53 00 56 00 42 00 49 00 6e 00 00 00 U.S.V.B.I.n...
Clipboard
dmVZQmdzOlUrcEBlRj87dHQ3USVBIn is interesting, perhaps it is the password we're looking for.
7z
Going back to the XML file we first encountered, we can see that there
were 2 7Zip files embedded in the Keepass database. However, after closer inspection
of 3620.dmp, we can actually find 10 7z headers present (37 7A BC AF).
By dumping each 7z file using hexedit we can try the password.
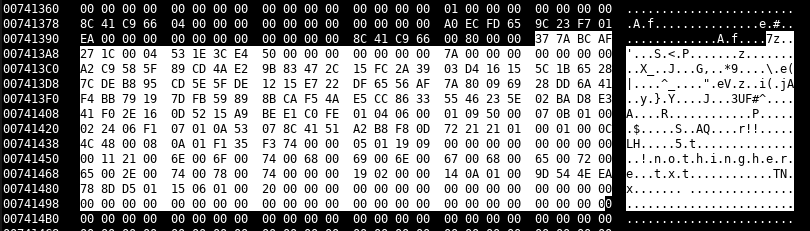
We create dumped.7zip from 0x7413A4 till 0x7414AF and extracted the contents using the password:
$ 7z x dumped.7zip
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
Scanning the drive for archives:
1 file, 268 bytes (1 KiB)
Extracting archive: dumped.7zip
WARNINGS:
There are data after the end of archive
Path = dumped.7zip
Type = 7z
WARNINGS:
There are data after the end of archive
Physical Size = 234
Tail Size = 34
Headers Size = 154
Method = LZMA2:12 7zAES
Solid = -
Blocks = 1
Enter password (will not be echoed):
Everything is Ok
Warnings: 1
Size: 72
Compressed: 268
$ cat nothinghere.txt
HackTM{d14c02244b17f4f9dfc0f71ce7ab10e276a5880a05fca64d39a716bab92cda90}
Flag
HackTM{d14c02244b17f4f9dfc0f71ce7ab10e276a5880a05fca64d39a716bab92cda90}